Web3 technologies are evolving at the speed of light, and it can be challenging to keep up with them or even understand the underlying concepts. As a total beginner passionate about the space, your best bet for understanding how Web3 works is to be well-versed in blockchain technology. The entire idea of Web3 is decentralization, taking authority away from centralized extensive tech systems and decentralizing it, thereby returning power to users. The blockchain enables this whole technology.
A blockchain is a method of storing a list of entries that, once created, cannot be easily changed. Blockchains do this with cryptographic concepts such as digital signatures and hash functions. The goal of blockchain is to eliminate the need for a central server by solving the problem of duplicate records. Blockchains also securely transfer items like money, property, and contracts without needing a third-party intermediary like a bank or government. It is extremely difficult to change data once recorded on a blockchain.
To explain further, let's liken the blockchain to an accounting book. A block in the blockchain is just a line item in the shared record book. Each time you add a new block to the chain, you add a new line to the book. The accounting record book can contain all kinds of information, not just limited to only crypto or financial transactions.
Many people are still perplexed by the relationship between bitcoin and blockchain. To clarify: blockchain is not Bitcoin; instead, it is the technology that powers Bitcoin. Bitcoin is a digital token, and the blockchain is the ledger that keeps track of who owns the digital tokens. Bitcoin cannot exist without a blockchain, but a blockchain can exist without Bitcoin.

Decentralization, transparency, immutability, and automation are all hallmarks of blockchain technology. Many industries can benefit from these components, resulting in many possible applications.
Blockchain Technology
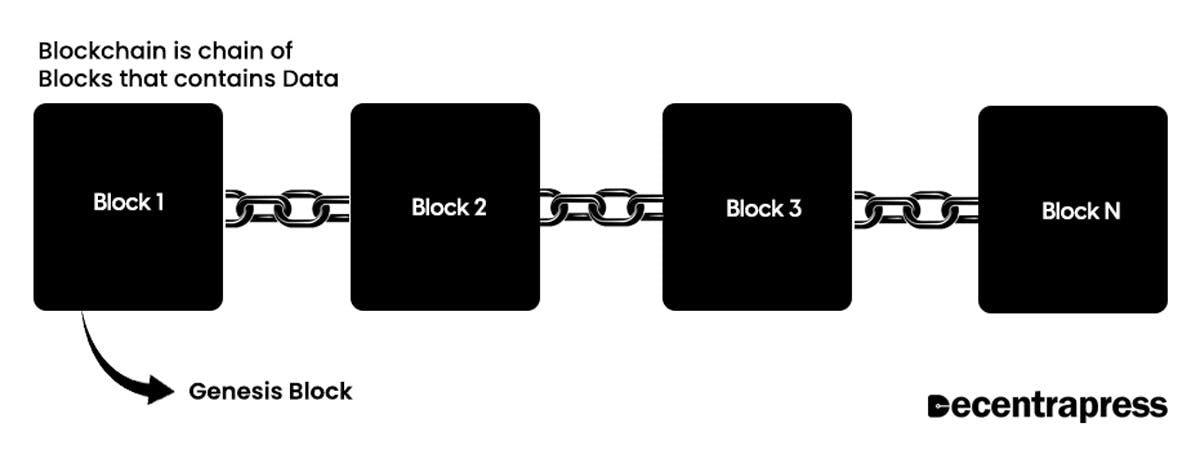
Let's now move a step ahead and study the Blockchain Architecture by understanding its various components. A blockchain, as the name implies, stores information in blocks. The type of blockchain determines the data stored within a block. For instance, the Bitcoin blocks include information about the sender, receiver, and the number of bitcoins being transferred.

The Genesis Block is the first block in the chain. Each new block in the chain links to the one before it.
Blockchain Hash Function
The hashing process involves jumbling up unprocessed data to such an extent that it is impossible to reassemble it into its original format. By hashing, you are taking a piece of data and sending it through a function, which then applies mathematical operations to the plaintext of the data. This function is known as the hash function, and the value or digest that it produces is referred to as the hash value.
A hash function converts an input string (numbers, alphabets, or media files) of any length into a fixed size. Depending on the hash function used, the set bit length can vary (for example, 32-bit, 64-bit, 128-bit, or 256-bit). The output with a fixed size is known as a hash. A hash algorithm's cryptographic byproduct is also this hash.
Because the Hash function is one-way, there is no way to recover the entire text from the generated hash. This differs from traditional cryptographic operations such as encryption, in which you can encrypt something using the key and then decrypt the message to its original form using decryption.
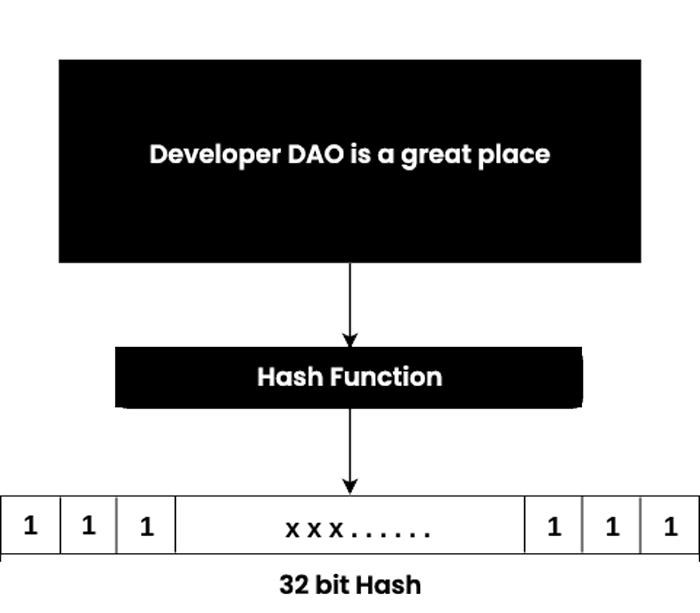
The hash algorithm has the following characteristics:
- It generates a one-of-a-kind output (or hash).
- It only works in one direction.
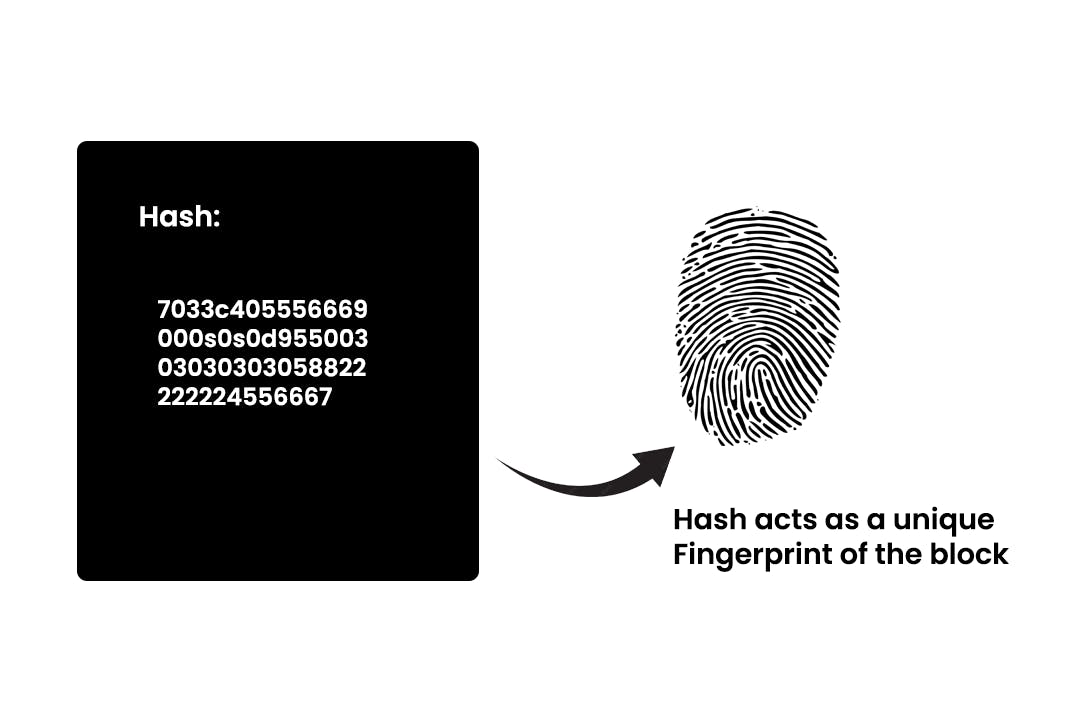
A hash is like a unique fingerprint for each block. It uniquely identifies a block and all of its contents. Once you create a block, any change within the block will change the hash. The Bitcoin blockchain employs the SHA-256 (Secure Hash Algorithm) hashing algorithm.
Each block in the blockchain contains:
- Data
- Hash
- Hash of the previous block
The hash is handy when you want to detect changes to block. If, by any chance, the fingerprint (hash) of a block changes, it does not remain the same block. If you want to have a strong understanding of how this works, please watch this video on YouTube.
Blockchain 101-A Visual Demo
This is an elementary visual introduction to the concepts behind a blockchain.
Part 2 is here:
If you are interested in playing with this on your own, it is available online at: anders.com/blockchain
Consider the following example, where we have a chain of 3 blocks. The first block has no predecessor. Block 2 contains a hash of block 1. While block 3 contains the hash of block 2
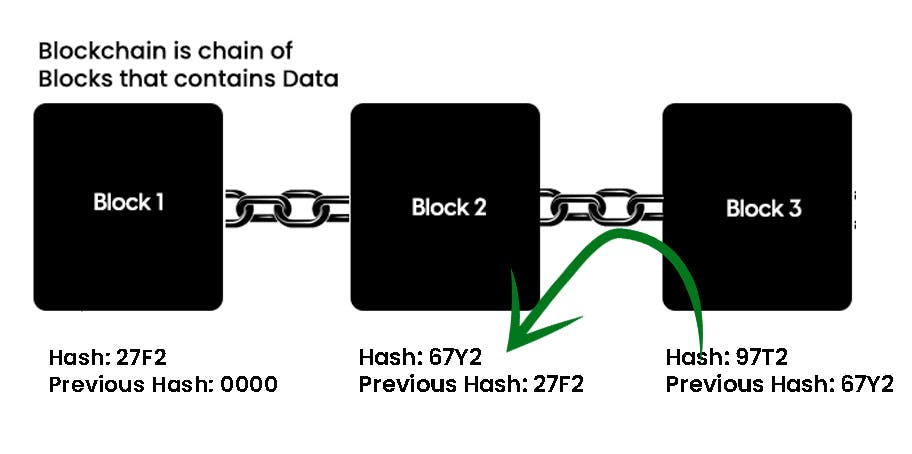
From the above diagram, it's clear that all blocks contain hashes of the previous block. This is the reason why blockchain technology remains so secure.
Let's now assume that an attacker changes the data present in block 3. This will force the hash of the block to change. Block 4 still contains the old hash of block 3. This will cause block 4 and other succeeding blocks to get invalid because they do not have the correct hash of the previous block.
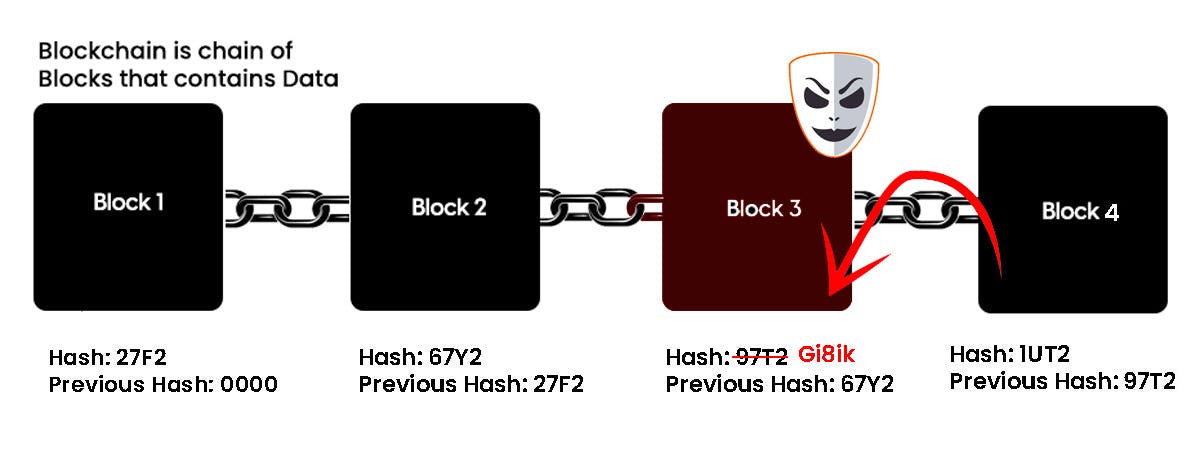
As a result, changing a single block can quickly render all subsequent blocks invalid.
Proof of Work
So far, we have seen that hashes are an excellent mechanism for preventing tampering. Still, nowadays, modern computers are super fast and can calculate hundreds of thousands of hashes per second. A hacker can tamper with a block in minutes and then quickly recalculate all the hashes of other blocks to make the blockchain valid again. Blockchains use the Proof-of-Work concept to avoid this problem. It is a mechanism that slows the production of new blocks. Proof of work is a consensus mechanism used to confirm that network participants, called miners, calculate valid alphanumeric codes (called hashes) to verify transactions and add the following block to the blockchain. The winning miner validates the block and earns a reward paid in cryptocurrency with proof of work. Crypto miners require support from vast networks of computers to quickly provide proof of work.
In the case of Bitcoin, calculating the required proof-of-work to add a new block to the chain takes nearly 10 minutes. In Bitcoin, a block contains more than 500 transactions on average. The average size of a block seems to be 1MB
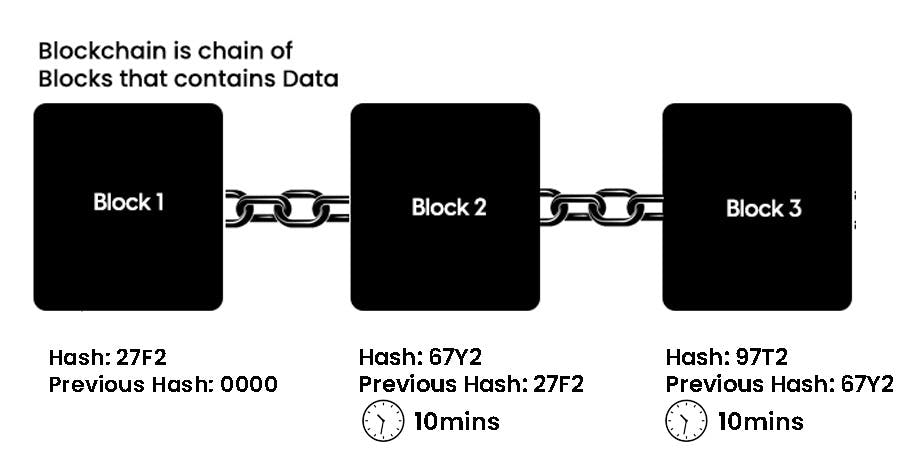
If a hacker wanted to change data in Block 3, he would first need to perform proof of work (which would take 10 minutes) before making changes in Block 3 and all subsequent blocks.
Because this mechanism makes it very difficult to tamper with the blocks, even if you tamper with a single block, you will need to recalculate the proof-of-work for all subsequent blocks. As a result, hashing and proof-of-work mechanisms ensure the security of a blockchain.
Distributed Peer-to-Peer Network
The blockchain also uses the distributed P2P network to secure itself, apart from hash functions and proof of work. Instead of relying solely on a central server or entity to manage the chain, blockchain employs a network system that anyone can join. When someone enters the network, they will get a full copy of the blockchain. Each person that joins the network is called a node.

Let's look at what happens when any user adds a new block. The winning miner will distribute the latest block to all the nodes. Each node must validate the block to ensure that it's genuine. After thorough verification, each node adds this block to its blockchain.
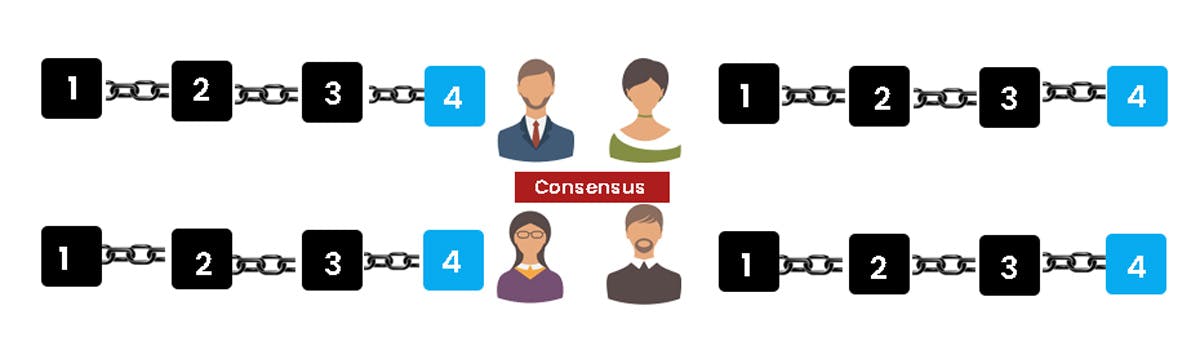
The nodes make it possible for Bitcoin to be used as a decentralized peer-to-peer (P2P) digital currency. Nodes are in charge of acting as communication hubs that can perform various tasks.
In the sense that they communicate with each other, any computer or device that connects to the blockchain can be considered a node. A node in virtual money is a computer linked to a cryptocurrency network and can perform tasks like producing, receiving, and moving data.
Together, all the nodes in the network create a consensus. They all agree about what blocks are valid and which ones are not. Any node in the network will reject any block that has been tampered with.
These characteristics are what ensure a blockchain's security. Because you must first tamper with all of the blocks on the chain before you can successfully tamper with it, then, for each, redo the proof-of-work. Following that, you gain control of more than half of the peer-to-peer network. After you've completed all of these steps, your tampered block will be accepted by everyone else. Of course, this is an almost impossible task.
Summary
The following is an overview of how blockchain technology works. When a transaction is requested, it could be cryptocurrencies, contracts, records, or any other type of data. The nodes will broadcast the requested transaction to a P2P network. The network of nodes validates the transaction and the user's status using well-known techniques. The new block is added to the existing blockchain after the transaction is complete. In a way that is both permanent and unchangeable.[Text]


